Why use a Network?
Quite simply explained we use networks for communication between computers, sharing of data and peripherals. In the business world we use networks for ease of administration and to cut costs.
Sharing data example imagine an office with 5 secretaries working on 5 different computers, one requires a file from another computer in a non networked office this file would have to be written to a portable media then loaded onto the computer. In a networked office the file could be accessed via the network from a shared folder.
Sharing peripherals example the same office with 5 secretaries working on 5 different computers, in order to print their work each computer would need to have a printer attached. In a networked office you could have one shared printer, cutting costs.
What do you need?
A common language or protocol (TCP/IP IPX/SPX, APPLE TALK) is a convention or standard that controls or enables the connection, communication, and data transfer between two computing endpoints.
A common language or protocol (TCP/IP IPX/SPX, APPLE TALK) is a convention or standard that controls or enables the connection, communication, and data transfer between two computing endpoints.
Cabling BNC,Cat5, fibre optic
Hardware NIC(Network Interface Card), router, switch, hub, modem wireless access point.
Network Service (DNS, WINS, DHCP).
Network Hardware
Network Interface Card
A network card, network adapter, network interface card or NIC is a piece of computer hardware designed to allow computers to communicate over a computer network. It has a MAC address. Every network card has a unique 48-bit serial number called a MAC address, which is written to ROM carried on the card. Every computer on a network must have a card with a unique MAC address. The IEEE is responsible for assigning MAC addresses to the vendors of network interface cards. No two cards ever manufactured should share the same address.
Hubs
An Ethernet hub or concentrator is a device for connecting multiple twisted pair or fibre optic Ethernet devices together, making them act as a single segment. It works at the physical layer of the OSI model, repeating the signal received at one port out each of the other ports (but not the original one). The device is thus a form of multiport repeater. Ethernet hubs are also responsible for forwarding a jam signal to all ports if it detects a collision. Hubs also often come with a BNC and/or AUI connector to allow connection to legacy 10BASE2 or 10BASE5 network segments. The availability of low-priced Ethernet switches has largely rendered hubs obsolete but they are still seen in older installations and more specialist applications.
Switches
A network switch or switch for short is a networking device that performs transparent bridging (connection of multiple network segments with forwarding based on MAC addresses) at full wire speed in hardware. As a frame comes into a switch, the switch saves the originating MAC address and the originating (hardware) port in the switch’s MAC address table. This table often uses content-addressable memory, so it is sometimes called the “CAM table”. The switch then selectively transmits the frame from specific ports based on the frame’s destination MAC address and previous entries in the MAC address table. If the destination MAC address is unknown, for instance, a broadcast address or (for simpler switches) a multicast address, the switch simply transmits the frame out of all of the connected interfaces except the incoming port. If the destination MAC address is known, the frame is forwarded only to the corresponding port in the MAC address table.
Hubs VS Switches
A hub, or repeater, is a fairly unsophisticated broadcast device. Any packet entering any port is broadcast out on every port and thus hubs do not manage any of the traffic that comes through their ports. Since every packet is constantly being sent out through every port, this results in packet collisions, which greatly impedes the smooth flow of traffic. A switch isolates ports, meaning that every received packet is sent out only to the port on which the target may be found (assuming the proper port can be found; if it is not, then the switch will broadcast the packet to all ports except the port the request originated from). Since the switch intelligently sends packets only where they need to go the performance of the network can be greatly increased.
Routers
A router is a computer networking device that forwards data packets across a network toward their destinations, through a process known as routing. A router acts as a junction between two or more networks to transfer data packets among them. A router is different from a switch. A switch connects devices to form a Local area network (LAN).
One easy illustration for the different functions of routers and switches is to think of switches as local streets, and the router as the junctions with the street signs. Each house on the local street has an address within a range on the street. In the same way, a switch connects various devices each with their own IP address(es) on a LAN. Routers connect networks together the way that on-ramps or major junctions connect streets to both main roads and motorways. The street signs at the junctions the (routing table) show which way the packets need to flow.
Wireless
Wireless Access Point (WAP) A wireless access point (AP) connects a group of wireless stations to an adjacent wired local area network (LAN). An access point is similar to an Ethernet hub, but instead of relaying LAN data only to other LAN stations, an access point can relay wireless data to all other compatible wireless devices as well as to a single (usually) connected LAN device, in most cases an Ethernet hub or switch, allowing wireless devices to communicate with any other device on the LAN.
Wireless Routers A wireless router integrates a wireless access point with an Ethernet switch and an Ethernet router. The integrated switch connects the integrated access point and the integrated Ethernet router internally, and allows for external wired Ethernet LAN devices to be connected as well as a (usually) single WAN device such as a cable modem or DSL modem. A wireless router advantageously allows all three devices (mainly the access point and router) to be configured through one central configuration utility, usually through an integrated web server. However one disadvantage is that one may not decouple the access point so that it may be used elsewhere.
Cables
Cable Terminology
10BASE2 (also known as cheapernet or thinnet) is a variant of Ethernet that uses thin coaxial cable. The 10 comes from the maximum transmission speed of 10 Mbit/s (millions of bits per second). The BASE stands for baseband signaling, and the 2 represents a rounded up shorthand for the maximum segment length of 185 metres (607 feet).
10BASE5 (also known as thicknet) is the original “full spec” variant of Ethernet cable. The 10 refers to its transmission speed of 10 Mbit/s. The BASE is short for baseband signalling as opposed to broadband, and the 5 stands for the maximum segment length of 500 metres.
10BASE-T is an implementation of Ethernet which allows stations to be attached via twisted pair cable. The name 10BASE-T is derived from several aspects of the physical medium. The 10 refers to the transmission speed of 10 Mbit/s. The BASE is short for baseband.The T comes from twisted pair, which is the type of cable that is used
100BASE-T is any of several Fast Ethernet 100 Mbit/s CSMA/CD standards for twisted pair cables, including: 100BASE-TX (100 Mbit/s over two-pair Cat5 or better cable). The segment length for a 100BASE-T cable is limited to 100 metres
Coaxial
Coaxial cable is an electrical cable consisting of a round conducting wire, surrounded by an insulating spacer, surrounded by a cylindrical conducting sheath, usually surrounded by a final insulating layer. It is used as a high-frequency transmission line to carry a high-frequency or broadband signal.
BNC connectors were commonly used on 10base2 thin Ethernet networks, both on cable interconnections and network cards, though these have largely been replaced by newer Ethernet devices whose wiring does not use coaxial cable.
CAT 5
Category 5 cable, commonly known as Cat 5, is an unshielded twisted pair cable type designed for high signal integrity. Category 5 has been superseded by the Category 5e specification. This type of cable is often used in structured cabling for computer networks such as Gigabit Ethernet, although they are also used to carry many other signals such as basic voice services, token ring.
Category 5 cable included four twisted pairs in a single cable jacket. It was most commonly used for 100 Mbit/s networks, such as 100BASE-TX Ethernet
Cat5 cable uses an RJ-45 (Registered Jack-45) connector at each end of the cable with a fixed wiring scheme. The ends are then crimped on to the cable
Wiring Scheme
Patch or straight through cables have Wiring scheme 1 at both ends of the cable and are used to connect computers to network wall sockets or hubs.
Crossover cables have Wiring scheme 1 at one end of the cable and Wiring scheme 2 at the other. These cables are used to connect network hardware together e.g. PC to PC, hub to hub.
Protocols
A protocol (TCP/IP IPX/SPX, APPLE TALK) is a convention or standard that controls or enables the connection, communication, and data transfer between two computing endpoints. Sending and receiving systems need to use the same protocol unless a gateway service sits between networks and translates from one to the other.
Most protocols specify one or more of the following properties:
- Detection of the underlying physical connection (wired or wireless), or the existence of the other endpoint or node
- Handshaking
- Negotiation of various connection characteristics
- How to start and end a message
- How to format a message
- What to do with corrupted or improperly formatted messages (error correction)
- How to detect unexpected loss of the connection, and what to do next
- Termination of the session or connectio
NetBIOS
NetBIOS is an acronym for Network Basic Input/Output System. The NetBIOS API allows applications on separate computers to communicate over a local area network. NetBIOS must be enabled for Windows File and Print Sharing to work.
NetBIOS provides three distinct services:
- Name service for name registration and resolution
- Session service for connection-oriented communication
- Datagram distribution service for connectionless communication.
Name service In order to start Sessions or distribute Datagrams, an application must register its NetBIOS name using the Name service. NetBIOS names are 16 bytes in length
Session service Session mode lets two computers establish a connection for a “conversation,” allows larger messages to be handled, and provides error detection and recovery. In NBT, the session service runs on TCP port 139.
Datagram distribution service Datagram mode is “connectionless”. Since each message is sent independently, they must be smaller; the application becomes responsible for error detection and recovery. In NBT, the datagram service runs on UDP port 138.
IPX/SPX (NWLINK)
Internetwork Packet Exchange (IPX) is the OSI-model Network layer protocol in the IPX/SPX protocol stack. The IPX/SPX protocol stack is supported by Novell’s NetWare network operating system. Because of Netware’s popularity through the late 1980s into the mid 1990s, IPX became a popular internetworking protocol. Novell derived IPX from Xerox Network Services’ IDP protocol. IPX usage is in general decline as the boom of the Internet has made TCP/IP nearly universal. Computers and networks can run multiple network protocols, so almost all IPX sites will be running TCP/IP as well to allow for Internet connectivity. It is also now possible to run Novell products without IPX, as they have supported both IPX and TCP/IP since NetWare reached version 5.
Sequenced Packet Exchange (SPX) is a transport layer protocol (layer 4 of the OSI Model) used in Novell Netware networks. The SPX layer sits on top of the IPX layer (layer 3 – the network layer) and provides connection-oriented services between two nodes on the network. SPX is used primarily by client/server applications.
NWLink is a IPX/SPX-compatible protocol developed by Microsoft and used in its Windows NT product line.NWLink is Microsoft’s version of Novell’s IPX/SPX Protocol. The Microsoft version of NWLink includes the same level of functionality as the Novell Protocol. NWLink includes a tool for resolving NetBIOS names.NWLink packages data to be compatible with client/server services on NetWare Networks. However, NWLink does not provide access to NetWare File and Print Services. To access the File and Print Services the Client Service for NetWare needs to be installed.
AppleTalk
AppleTalk is a suite of protocols developed by Apple Computer for computer networking. It was included in the original Macintosh (1984) and is now used less by Apple in favour of TCP/IP networking.
AppleTalk contains two protocols aimed at making the system completely self-configuring. The AppleTalk address resolution protocol (AARP) allowed AppleTalk hosts to automatically generate their own network addresses, and the Name Binding Protocol (NBP) was essentially a dynamic DNS system which mapped network addresses to user-readable names.
For interoperability Microsoft maintains the file services for Macintosh and the print services for Macintosh
TCP/IP
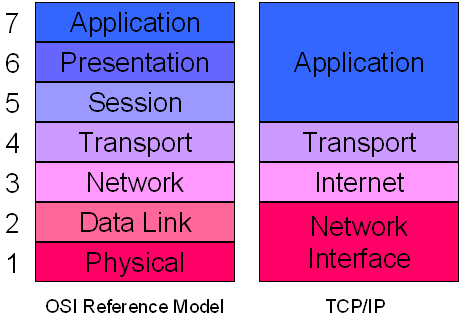
The Internet protocol suite is the set of communications protocols that implement the protocol stack on which the Internet and most commercial networks run. It is sometimes called the TCP/IP protocol suite, after the two most important protocols in it: the Transmission Control Protocol (TCP) and the Internet Protocol (IP), which were also the first two defined.The Internet protocol suite like many protocol suites can be viewed as a set of layers, each layer solves a set of problems involving the transmission of data, and provides a well-defined service to the upper layer protocols based on using services from some lower layers. Upper layers are logically closer to the user and deal with more abstract data, relying on lower layer protocols to translate data into forms that can eventually be physically transmitted.The OSI model describes a fixed, seven layer stack for networking protocols. Comparisons between the OSI model and TCP/IP can give further insight into the significance of the components of the IP suite, but can also cause confusion, as TCP/IP consists of only 4 layers.
The four layers in the DoD model, from bottom to top, are:
- The Network Access Layer is responsible for delivering data over the particular hardware media in use. Different protocols are selected from this layer, depending on the type of physical network.
- The Internet Layer is responsible for delivering data across a series of different physical networks that interconnect a source and destination machine. Routing protocols are most closely associated with this layer, as is the IP Protocol, the Internet’s fundamental protocol.
- The Host-to-Host Layer handles connection rendezvous, flow control, retransmission of lost data, and other generic data flow management. The mutually exclusive TCP and UDP protocols are this layer’s most important members.
- The Process Layer contains protocols that implement user-level functions, such as mail delivery, file transfer and remote login.
Network Services
DNS (Domain Naming System)
The Domain Name System (DNS) stores and associates many types of information with domain names, but most importantly, it translates domain names (computer hostnames) to IP addresses. It also lists mail exchange servers accepting e-mail for each domain. In providing a worldwide keyword-based redirection service, DNS is an essential component of contemporary Internet use.
The DNS pre-eminently makes it possible to attach easy-to-remember domain names (such as “es-net.co.uk”) to hard-to-remember IP addresses (such as 270.146.131.206). People take advantage of this when they recite URLs and e-mail addresses.
WINS (Windows Internet Naming Service)
Windows Internet Naming Service (WINS) is Microsoft’s implementation of NetBIOS Name Server (NBNS) on Windows, a name server and service for NetBIOS computer names. Effectively, it is to NetBIOS names what DNS is to domain names – a central mapping of host names to network addresses. However, the mappings have always been dynamically updated (e.g. at workstation boot) so that when a client needs to contact another computer on the network it can get its up-to-date DHCP allocated address. Networks normally have more than one WINS server and each WINS server should be in push pull replication; the favoured replication model is the hub and spoke, thus the WINS design is not central but distributed. Each WINS server holds a full copy of every other related WINS system’s records. There is no hierarchy in WINS (unlike DNS), but like DNS its database can be queried for the address to contact rather than broadcasting a request for which address to contact. The system therefore reduces broadcast traffic on the network, however replication traffic can add to WAN / LAN traffic.
DHCP (Dynamic Host Configuration Protocol)
The Dynamic Host Configuration Protocol (DHCP) automates the assignment of IP addresses, subnet masks, default routers, and other IP parameters. The assignment usually occurs when the DHCP configured machine boots up or regains connectivity to the network. The DHCP client sends out a query requesting a response from a DHCP server on the locally attached network. The DHCP server then replies to the client with its assigned IP address, subnet mask, DNS server and default gateway information.The assignment of the IP address usually expires after a predetermined period of time, at which point the DHCP client and server renegotiate a new IP address from the server’s predefined pool of addresses. Configuring firewall rules to accommodate access from machines who receive their IP addresses via DHCP is therefore more difficult because the remote IP address will vary from time to time. Administrators must usually allow access to the entire remote DHCP subnet for a particular TCP/UDP port. Most home routers and firewalls are configured in the factory to be DHCP servers for a home network. ISPs (Internet Service Providers) generally use DHCP to assign clients individual IP addresses.DHCP is a broadcast-based protocol. As with other types of broadcast traffic, it does not cross a router.
APIPA (Automatic Private IP Addressing)
If computers are unable to pick an address up from a DHCP server they use Automatic Private IP Addressing (APIPA). This means the computer will assign itself a random address between 169.254.0.1 – 169.254.254.254/16, allowing it to communicate with other clients who are also using APIPA.
Automatic Private IP Addressing (APIPA), this allows unknowledgeable users to connect computers, networked printers, and other items together and expect them to work. Without Zeroconf or something similar, a knowledgeable user must either set up special servers, like DHCP and DNS, or set up each computer by hand.
Networks
LAN :
A Local Area Network (LAN) is a computer network covering a small local area, like a home, office, or small group of buildings such as a home, office, or college. Current LANs are most likely to be based on switched Ethernet or Wi-Fi technology running at 10, 100 or 1,000 Mbit/s.The defining characteristics of LANs in contrast to WANs (wide area networks) are: their much higher data rates; smaller geographic range; and that they do not require leased telecommunication lines.
PAN :
A Personal Area Network (PAN) is a computer network used for communication among computer devices (including telephones and personal digital assistants) close to one person. The reach of a PAN is typically a few metres and may use Bluetooth, wireless or USB for connection.
WAN :
A Wide Area Network (WAN) is a computer network covering a wide geographical area, involving a vast array of computers. This is different from personal area networks (PANs), metropolitan area networks (MANs) or local area networks (LANs) that are usually limited to a room, building or campus. The most well-known example of a WAN is the Internet. WANs are used to connect local area networks (LANs) together, so that users and computers in one location can communicate with users and computers in other locations.